With its dependency on legacy and often decades-old equipment, controllers, and systems, the industrial manufacturing sector has been slow to embrace the complete digital transformation undertaken by other industries. But that is changing. Hastened by the pandemic, the arrival of Industry 4.0, or the Fourth Industrial Revolution, has brought a new urgency for industrial manufacturing to incorporate artificial intelligence (AI) and the Internet-of-things (IoT) into its processes. Driven by the demand for real-time monitoring, analytics, reporting, and machine-to-machine (M2M) communications, the global Industrial IoT (IIoT) market is expected to grow by more than 23% through 2030. Additional competitive and market pressures to enable remote workers, hybrid-business models, IT interoperability, greater automation and the shift to more robotic and collaborative robotic (cobot) systems have further accelerated the speed and velocity of digitization. While this represents a potential boon for manufacturers and opens the door to various new opportunities, it also comes with an equal number of challenges. One of the biggest for industrial manufacturing is security.
The Threat Posed by Ransomware and Other Attacks is Only Increasing
The rapid rise and spread of the digital, interconnected world have left much of the public and private sectors exposed and unprepared to deal with a whole new range and class of security threats. For manufacturers, the convergence of legacy operational technology (OT) and new, advanced IoT with core (and increasingly cloud-based) IT networks makes their systems especially vulnerable . You needn’t look far or hard for examples illustrating the high cost and broad scope of the problem, with the Colonial Pipeline breach being the most recent and notorious. In 2022, attacks by ransomware groups across industry increased by 29%, with manufacturing being the primary target for over a quarter. By some estimates, the cost to manufacturers in downtime exceeded $5.53 billion (US) alone.
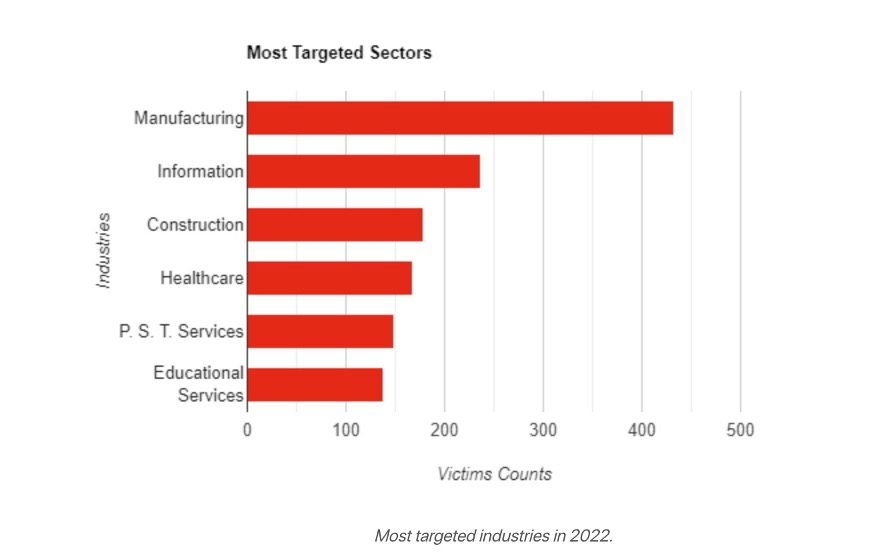
With ransomware attacks in the news and wreaking havoc at home and across the globe, it’s easy to forget that they’re just one of the many cyber threats manufacturers face. In addition, manufacturers must confront all kinds of other external and internal threats, ranging from unintentional access and exfiltration to the theft of sensitive IP and customer data. The fallout from a breach can have dire and lasting ramifications, including damage to physical infrastructure, substantial financial cost, loss of reputation and standing, or even death. The 2017 Triton attack on a Saudi Arabian petrochemical plant, for example, directly targeted critical safety systems and could have led to catastrophic loss of property and life if not thwarted.
Legacy OT Security is No Match for Today’s Cyber Threats
While manufacturers have long relied on digital technology to mechanize and automate their shop floors, the legacy OT, IT and business systems that make up their tech stacks were not designed for today’s security threats. Legacy OT and industrial control systems (ICS), which were built for monitoring and are typically incompatible with traditional IT endpoint security, are particularly problematic. In a recent survey, 86% of manufacturers reported having inadequate visibility into their ICS, rendering them deaf, dumb, and blind to the most common attacks. The problem is so acute that the U.S. Cybersecurity and Infrastructure Agency (CISA) recently issued an alert warning manufacturers of the vulnerabilities to their ICS and SCADA systems.
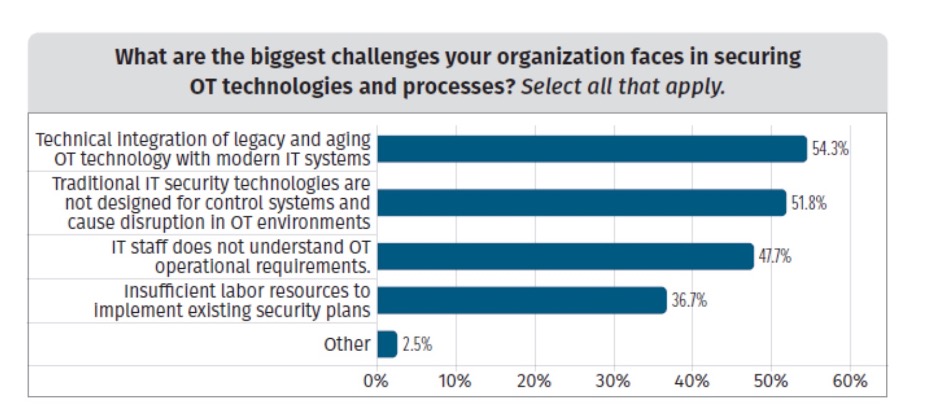
As manufacturers are discovering, there are few easy answers. Unsecured and proprietary protocols, plus high-availability requirements, make legacy ICS systems notoriously difficult to retrofit or upgrade. In addition, traditional tactics like air gapping are no longer effective or feasible, given the real-time connectivity demands of IIoT. Add in that IT teams typically are siloed from OT and lack the updated security skills and resources to take on today’s threats, and you have the makings of a disaster.
The Case for IT-OT Integration
For manufacturers looking to secure their technological infrastructure, there’s really only one way forward: Cloud modernization with centralized OT and IT, backed by built-in redundancy and zero trust network access (ZTNA). With the number and variety of bad actors and threats only increasing, manufacturers have to assume that no level of security, no matter how rigorous, can protect them completely. At some point, their systems will be breached. To ensure continuity, their IT and OT systems must not only be secure but redundant. A modern cloud architecture that consolidates IT and OT computing and security on one platform enables the segmentation, monitoring, and redundancy needed to quickly identify, quarantine, and restore operations regardless of the threat or situation. Cloud solution providers are able to spend orders of magnitude more on securing their cloud infrastructure than any one manufacturer can. Their business depends on it.
Until now, most manufacturing technology architecture has been predicated on the Purdue model, which segregated OT systems from network IT using air-gapping and other techniques. The real-time connectivity demanded by today’s IIoT renders these obsolete. However, modern cloud platforms provide new and advanced ways to segment and segregate OT, pushing Purdue into the 21st century, while maintaining the connection to essential IT and business systems. Modern cloud security is predicated on zero trust (ZTNA) protocols, which assume every endpoint and connection is insecure and deploys methods like encryption, multi-factor authentication, access controls, and virtual private clouds (VPCs) to lock down the network. The integration of the secure cloud with OT allows manufacturers to apply these strategies to their shop floors without exposing them to cyber threats.
As manufacturers start to integrate and secure their IT and OT systems, a number of core best practices are emerging. Chief among those is the migration of SIEM (security information and event management) and all system monitoring and analytics onto one cloud platform, giving users a single, holistic view of their entire tech infrastructure. Another is the use of gateways and edge computing to segment devices or zones and provide the low-latency computing, end-point protection, event monitoring, and reporting required. A third is the implementation of a centralized data governance regime that ensures consistent access policies and controls across the organization. Tying all these together is the imperative to centralize or consolidate, which is key given the interconnected nature of modern manufacturing and increasing demands to leverage these data streams from the shop floor in business systems like ERP.
Getting Started with Enterprise-Level Security
With today’s increased demand for innovation and efficiency, manufacturers can no longer afford to isolate their OT from their IT and business systems. What happens upstream and is recorded or reported in, say, your ERP has a direct impact on your downstream manufacturing or assembly facilities and vice versa. While connecting your systems is now mandatory, doing so without enterprise-cloud security will leave you vulnerable to the ransomware attacks and other threats documented above. As a result, any digital transformation initiative needs to consider every part of the system. Incorporating a cloud-based ERP solution, like Rootstock ERP on Salesforce, that can leverage the enterprise-level security of the Salesforce Cloud Platform gives both the visibility and security needed to compete and remain safe in today’s challenging and insecure environment.